
If you're arriving here after having your longstanding Facebook account suspended without notice or cause, happy new year! An untold number of Facebook users, myself included, kicked off their much-anticipated holiday break to the shock of of a suddenly disabled account. Individual experiences vary, but I'm making this post to compile a running record while digging deeper into the technicalities of the attack and any potential recourse to get our wrongfully disabled accounts restored.
The Facebook Suspended and Disabled Notices
Attempting to login, if even tangibly successful, may yield the most vague error imaginable.
Account Disabled
Your account has been disabled. If you have any questions or concerns, you can visit our FAQ page here.

This is the notice that I was greeted with upon clicking "Forgot Password" when attempting a login after the incident, at least on some devices. With this level of disable, there is no way to download your profile data or submit any form of appeal. This is what Facebook deems "permenantly disabled." Clicking on the FAQ page link provides a generalized list of possible reasons an account might be disabled, not specific to the individual.
Others who are not quite at this level of extremes may see a slightly more detailed error:
Your account has been disabled
Your account was disabled on [Mon DD, YYYY]. If you think your account was disabled by mistake you can submit more information via the Help Center for up to 30 days after your account was disabled. After that, your account will be permenantly disabled and you will no longer be able to request a review.
- Go to Help Center
- Download Your Information

Eventually, the root of these disabled accounts may reveal itself if you're able to get through the ID verification process and log back into Facebook using a temporary code:
We suspended your account
Your Facebook account was suspended because your Instagram account [gibberish fake Instagram account name that you never knew about] doesn't follow our rules.
You have [180] days left to appeal. Log into your linked Instagram account to appeal our decision.
- Download your information
- Log into your Instagram account

I was able to arrive at the screen above after clicking "Try Another Way" from the inaccessible 2FA screen when attempting my normal sign-in. Upon submitting ID verification and waiting up to two days, Facebook began sending emails with temporary codes and links to "get back into your account."

The hyperlinks and codes within these emails did not help when attempting from my desktop computer or any Facebook-related app. Instead, I had to access the link from the "Reminder" email in my mobile browser (Chrome) where it bypassed the 2FA and other login criteria to reach that suspended notice screen. These links may also only work once before going haywire again and kicking you back out to the "disabled" screen.
And yes, Facebook is telling victims of this attack that in order to appeal, you are supposed to log into the fake, non-existent malicious scam Instagram account that was unknowingly linked to your real Facebook account and that you only have 30-180 days to do so.
Still others have suspension notices that give other particular causes. From the very vague "community standards" violation to horrifyingly accusatory ones like "child exploitation." These alternative notices still tend to relate to what the attacker spammed through the maliciously linked accounts before Facebook's bots and AI system took notice and blanket disabled everything including the victim's real account.
Hack Origins (Fake Instagram Linked Account)
While account suspensions can arise from any number of real or imagined offenses (thanks to demonstrably less-than-perfect AI and bot-related screening processes across Facebook) one of the most common recent attacks that leads to these widespread account locks is from a rogue Instagram bot/malicious user who links their spambot account(s) to your legitimate Facebook account.
This is achieved through Meta's "Accounts Center" that includes components to share login and feed data across the Metaverse including Facebook, Instagram, Oculus etc. They call such linkage "connected experiences." The convenience of this, including shared sign-in and one-click sharing across multiple feeds, conversely creates an alarmingly vulnerable attack vector. Whereby any account in that linked chain that gets compromised will in turn make the associated ones just as vulnerable and exploitable by the intruder.
In most of these scenarios, the hacker/attacker begins by generating fake Instagram profiles designed to spam revenue-generating click farm ads or other financially-motivated, malicious content. From there, they might test leaked credentials from the multitude of continuous largescale data breaches to see which real victim accounts are inadequately secured and accessible to latch onto via Instagram or Facebook. This could even be done well in advance of their actual use, to surreptitiously create sleeper bot accounts that at any moment could be used to share malicious content through the victim's legitimate Facebook account.
Stories detailing these linked Instagram exploits and disabled accounts that arose from it began by early-2023, if not earlier.
MAY 2023: Facebook users lose access after violations of linked spam Instagram accounts they don’t own
Session and Cookie Hijacking
It is a common misbelief that "My Account was Hacked!" equates to a criminal stealing someone's direct login credentials through malware or data leaks, allowing them to impersonate the victim merely by logging in directly. But in this advent of two-form authentication (2FA), such tactics aren't always successful unless the attacker also has access to the victim's phone and/or email address. Some fraudsters are brazen enough to convince the most vulnerable to send them the security codes directly, despite the texts and emails themselves advising the user to NEVER give the codes to anyone.

But what if all of these security measures could be bypassed outright? That's the scary premise behind cookie impersonation and cookie hijacking, also known as session hijacking, and what I believe evidence shows has been happening to countless Facebook accounts for at least 18 months now. The premise of this is that attackers can clone one's browser cookies, including active login sessions on Facebook etc., to their own device in order to trick the platforms into believing it is still the original active session by the account owner.
This concept is far from new. Meta's own engineering team blogged about it on May 3, 2023 and noted the discovery of such targeted exploits already by January 2023.
In late January 2023, our security team identified a new malware NodeStealer that targeted internet browsers on Windows with a goal of stealing cookies and saved usernames and passwords to ultimately compromise Facebook, Gmail, and Outlook accounts.
Other security articles were written about the concept much earlier, even as far back as the 1980s for a slight variant of modern day cookie hijacking. One from Security Intelligence (April 5, 2021) goes into more depth in explaining the premise, dangers and potential protection mechanisms.
Cookies are powerful, and in some cases, more so than passwords. With the right cookies, attackers can gain unlimited access to resources. If you’re a victim of cookie hijacking, MFA won’t help you.
General Methods of Attack
The exact exploit used in this Instagram-Facebook attack was not immediately obvious. It afflicted an undetermined amount of users across the world, from casual members to senior level IT professionals. The latest rash of disabled accounts appears to have amplified in the last half of December. In Spanish-speaking countries, so many have been left without their account starting around December 18th that they have started a #MetaResponde trend on X hoping to get a response from Meta (as of December 31, 2024, Meta/Facebook/Instagram have not publicly responded). The Reddit group FacebookDisabledMe has around 22,500 members, up from 20,000 when I first browsed it.

In general terms, traditional execution concepts of hacks, trojans, viruses and malware apply to cookie theft as well. The content can be passed along to attackers through runaway browser extensions, browser or API vulnerabilities, operating-system level scripts including those powered by JavaScript and Node.js, or any typical file-stealing methodologies. Last year, a purported "ChatGPT for Google" browser extension downloaded thousands of times was devised to steal Facebook session data, specifically.
Once installed, the extension leverages the
onInstalledhandler function to harvest Facebook session cookies. It then encrypts them with an AES key and exfiltrates the data to the attacker’s server using a GET request.After decrypting the stolen cookies, threat actors can use them to log in to the victims’ Facebook accounts with full ownership rights. As BleepingComputer reports, perpetrators use hijacked accounts to run malvertising campaigns and spread banned materials such as ISIS propaganda.
Likely Culprit: Compromised Chrome Extensions (e.g., Reader Mode)
I spent several days combing over what could be the culprit. I hadn't installed any new browser extensions in ages and felt confident in the ones that I had. They were well-trusted and widely used. At first I suspected my cookie session data was stolen after running various legacy Python script installers on MacOS to help restore and unlock an old 4th generation iPad. However, I reviewed all of that code and nothing malicious was contained in it. [Side note: The official site of Apple Tech 752, maker of Sliver and other iOS unlock tools, used "best-links" for hosting many of its files and that site is now taken over, toxic and full of redirects, presumed malware and phishing, viruses etc. so avoid it at all costs!]
On December 29, The Hacker News published an article: "Dozens of Chrome Extensions Hacked, Exposing Millions of Users to Data Theft." This, in turn, referenced a technical analysis by Cyberhaven of the origins of this compromise via a phishing attack to allow injection of malicious extension updates via the Google Chrome Web Store. The initial response and summary of the Cyberhaven-specific breach can be read here. In short, THN summarizes that "the malicious code targeted identity data and access tokens of Facebook accounts, primarily with an intent to single out Facebook Ads users."

While a cursory review of my extensions revealed Reader Mode as one offending extension, at least according to the list by THN, the timing of that (exploited Dec. 24-26) doesn't align with my account compromise occurring on Dec. 20. However, John Tuckner (Secure Annex) also told THN: "there is a possibility that the campaign has been ongoing since April 5, 2023, and likely even further back based on the registration dates of the domains used." So I am reasonably confident to conclude some other Chrome extension between my various devices and profile sessions may have had similar compromises, possibly including stale extensions on my much less used MacOS..
Mapping the Attack
Assuming you can eventually reach the screen of your Facebook suspension/disabled account that contains the "Download Your Information" button, you'll want to download that ZIP file and save it to a safe location. But don't set your expectations too high that it will be a pristine copy of your entire social presence. In my case, the downloaded file was a paltry 3MB and contained only my profile photos and some basic account metadata. A far cry from the more then 5GB of data my true Facebook profile amassed since the late-2000s.
Even so, there are breadcrumbs of clues we can glimpse to better develop the timeline of attack.

Profile URL, Username, Email Addresses, Family
Meta Support will ask for your account's URL or username and may also want to know what email was associated with it. If you are unsure of this or want to confirm, you can find this within:
personal_information > profile_information > profile_information.html
It will show the direct hyperlink to your profile as well as other important details such as initial account creation date, all the emails you've linked to it over time, phone numbers, and associated family members if you set that up in your profile. This can be useful evidence to screenshot and share as part of proving you are the owner of the account, or even if having to work through a family member's account to reach elevated support.
Account Activity (Pinpointing the Breach)
Let's see what we can discover about the user(s) who overtook the account moments before it was disabled.
security_and_login_information > account_activity.html
Important to note the time zone that is indicated at the top of the page (e.g., "UTC+07:00") to translate Facebook server log time to your own local time to make sense of precisely when the hack and disabling occurred.
The latest account session activity is shown beginning from the top, in descending order. In my case the topmost entry was "API Session Terminated" from my own IP and location, and this would be when Facebook Messenger was fully logged out and all connections deactivated. But the entries beneath that one, and before the next local one that is verified as my IP and region, are of most importance.

Here I observed three session-related entries with an origin of Douala, Littoral Region, Cameroon (Africa). Note that in attacks like this, it is typical that the offender will use VPNs so the location and IPs are not necessarily accurate. Still, they depict abrupt and major deviance from ordinary account usage.
- (ATTACKER) Web Session Terminated (Dec 21, 2024 4:03:48 am)
- (ATTACKER) Web Session Terminated (Dec 21, 2024 4:01:47 am)
- (ATTACKER) Session Updated (Dec 21, 2024 3:57:30 am)
Even more importantly, the initial "Session Updated" from the attacker and the last "Web Session Terminated" by them prior to the account being disabled, references the same session cookie (e.g., "emXK******"). that my own local desktop browser was using. This is more evidence that the hack occurred via cookie hijacking, not direct login or stolen credentials.
Beneath those three attack-point entries, resumes my ordinary session login data and nothing abnormal. My mobile phone performed a regular "Session Update" itself at Dec 21, 2024 3:31:04 am, approximately a half hour before the attack occurred.
Account Disabled Timestamp
It is important to document exactly when your account was hacked and disabled, including for support-related interactions. While you can give ballpark estimates, it is possible to find precise data here:
security_and_login_information > account_status_changes.html
If your account was disabled, it will show the timestamp again using UTC+07:00 (server time).
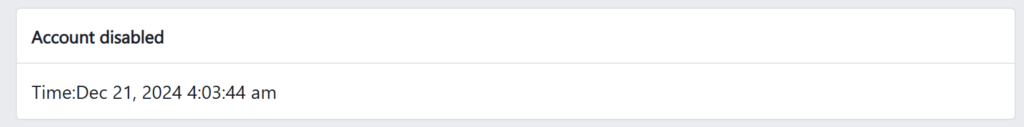
In my case, it reads: "Time:Dec 21, 2024 4:03:44 am"
Piecing this together with the session data above, the timeline for my scenario is (in UTC-7 time):
- My account was behaving normally as of Dec. 21, 2024 at 2:49:15 a.m. (UTC-7) and all services operational.
- My authentic desktop Chrome-based session was noted as "Session Updated" on Dec. 21, 2024 at 3:31:04 a.m. (UTC-7) I was not actively browsing Facebook but did have my browser open.
- Initial cookie hijacking occurred on Dec. 21, 2024 at 3:57:30 a.m. (UTC-7) (Using a clone of my original logged in desktop cookie and an foreign IP based in Africa).
- Attacker's 'Web Session A' terminates on Dec. 21, 2024 at 4:01:47 a.m. (UTC-7) (This used a unique session cookie and likely was the moment they completed the "link" to the fake Instagram account.)
- Facebook disables my account on Dec. 21, 2024 at 4:03:44 a.m. (UTC-7)
- Attacker's 'Web Session 'B' terminates on Dec. 21, 2024 4:03:48 a.m. (UTC-7) (This was again the clone of my original desktop cookie and was terminated as a result of the overall account disabling 4 seconds prior.)
- This hack and exploit occurred within a span of 7 minutes (Dec. 21 3:57:30 a.m. to 4:03:48 a.m. UTC-7) without any indication or alerts to me, since they used session hijacking to mimic my active session from their system across the world. My Facebook account was then inaccessible and disabled, with a listed reason of the suspension being the rogue Instagram account p9npvdn linked to it.
The takeaway here is that we can see the attacker may have acted for only a couple of minutes before Facebook's system detected the malicious content, ads or whatever else they had propagated through the fake Instagram account and my unknowingly linked Facebook profile.
I imagine those few moments included mass circulation of some revenue-generating clickthrough farms or other scamware payloads across Instagram and Facebook platforms, using the linked account to blast content to both as fast as possible. Enough for Facebook's automated system to flag it and disable everything.
Two-Factor Authentication
Although we have established that the session hijacking approach to this hack can circumvent 2FA, it is still reasonable to establish a record that your account did (or did not) have that enabled when weeding through support tickets and questions. This can be found in:
security_and_login_information > two_factor_authentication.html

I had enabled 2FA back in 2022, which at the time would had been Facebook's own encouraged "Code Generator" system. But, surprise, they have discontinued this in favor of other authenticators. I am not sure where that leaves me, even if my account were restored, since it asks for 2FA on login but I have no other known authenticator setup and relied on having Facebook sessions one place or another to verify. But this at least establishes proof that I did what I could to keep my account secured, and that myself and the countless others had no control over the ultimate exploit of linking a malicious Instagram account to our authentic Facebook ones.

The Meta Ads Connection
Users who manage to reach the point of account restoration are also often surprised to discover one or more advertisement campaigns setup under their Meta or Business account. This is a common payload by the attackers, to spread unknown ad/malware-laced content via paid advertisement using the real Facebook account's existing ties with Meta or Facebook Business, which may include credit cards already on file.

I suspect this is exactly what has happened with my account, as I began receiving several Meta for Business emails days after the attack. They were framed as offering tips and alluding to some rejected ads. Catch 22: I have no access to the aforementioned Meta account to even review any of this, which is synonymous with my disabled Facebook account. Users who have credit or debit cards on file and have been impacted by this exploit will want to keep a close eye on their card statements.
Deeper Dive into the Malvertising Fraud
After recovering my Facebook account, I was both intrigued and horrified by what was occurring using my profile's Ad Manager as a conduit — from the day it was disabled until long after it was reactivated. In this process I uncovered layers upon layers of fraud.
As soon as my account came back to life, I took note of an endless stream of notifications about Meta ads being charged and rejected. Thousands and thousands of dollars worth over the course of two weeks.

Attempting to click onto any of the ads or review the context behind them resulted in failure, since Meta had also disabled my personal ad account as a result of all the other ensuing chaos.

I wrongly assumed that since my account had been restored using a fresh email account, that the fraudulent ad campaigns would come to an immediate halt. Imagine my surprise when I continued receiving new notifications about additional ads and charges all through the night and into the next day. After I removed every linked credit card from my profile including several unknowns (presumed stolen) that were added by the attacker, the billing section of Ads Manager indicated I owed them $577.54.

The list of previously completed transactions on the billing page expressed that the scammers had been spreading more than $1000 of ads a day and paying for them using unknown cards to me. They had purchased $10,158.70 of malicious ad space between December 22 and January 3.

Despite indicating that the ad account had been disabled for "unusual activity" the ads continued being served, without delay. At this point I still had no idea what the ads even were, since I was unable to access the ad dashboard, administration screens or any other crucial area of the website. Reaching almost any page of the ad manager would throw only vague errors like "something unexpected happened" and "you will be unable to modify any ads in this account."
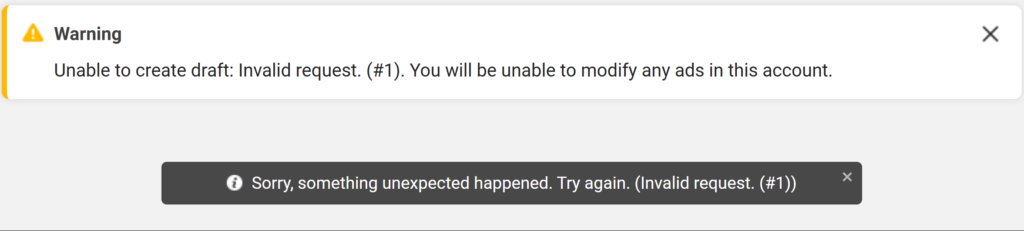
The scammer's hijacked ad profile linked to my account was called "250mon sold 7" and, again, despite being fully disabled was still serving up ads and accumulating additional charges continuously even after I had regained control. To add, when I checked in the morning the $577 outstanding balance had been paid with another credit card that had somehow been added to my account despite it being fully secured and with no other sign-in attempts or sessions. Peculiar, I thought.

Eventually I managed to get into the administrative sessions of the ad manager, and suddenly it made more sense. The attacker, after linking the malicious Instagram account to breach into my authentic Facebook with Meta Ads account, added five additional ad account admins and analysts to my account. So even before I had even regained control of my own account and ad manager, they could tap into any of the false admin accounts to continue pushing new ads, adding credit cards and so on.

Had they been closely monitoring the page, I suspect they could had again "removed" me as administrator to continue on without my ability to intervene. I instead was able to successfully remove each of the offending accounts, which finally took the ad campaigns and card additions to a true close.
Substance of the Scam Ads
As I continued grinding my way through the maze of ad management related pages, I was for the first time able to glimpse what sort of ads were being illicitly and unknowingly served via my ads account. 21 ads were rejected for "Online Gambling and Games" or "Fraud, Scams and Deceptive Practices" reasons.


The ads were cleverly packed up for distribution via a new fake page masquerading as an ordinary Facebook user. That page was injected between many actual pages that I own or manage, and has administrators in China and India. As of this writing, the page still exists and is now presumed to be a dormant "sleeper" account that the hackers may revive at another point in time. Other clones of this page also exist with admins in Hong Kong, with different names but the same purported New York location.

Every imaginable sort of ad placement on Facebook, Instagram and Messenger was ordered across thousands of entries, largely targeting Brazil. The majority of ads depicted a fictitious gambling app "Super Mega Ganho 630.610" and can be seen below. The final attempted campaign to run was created on January 3, 2024 and titled: "Promoting Stefania Mariana Helen" with a target audience of China.
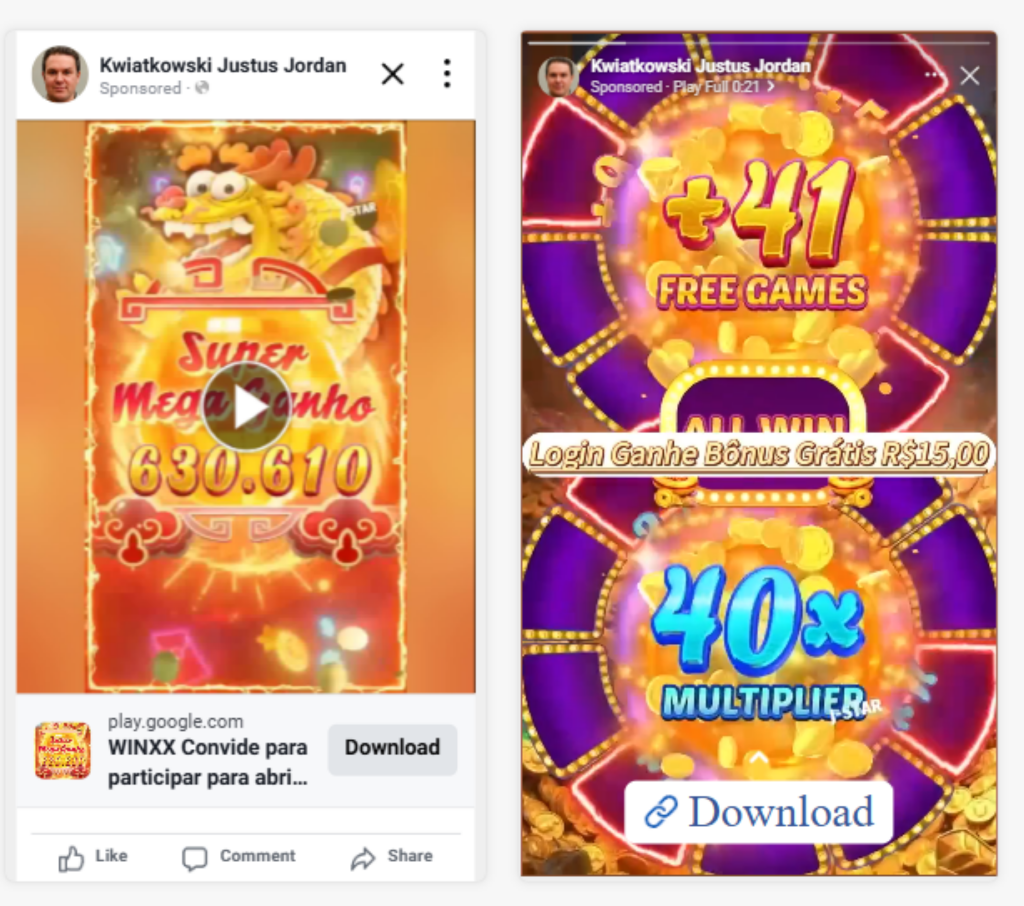
Note how the ads include an apparent link to play.google.com so the unsuspecting user may tap it expecting to arrive to an Android app in the Google Play store. But not so fast! Facebook's ad campaign allows advertisers to specify both an actual Website URL and a Display Link. This allowed the fraudsters to impersonate legitimate Google Play app ads but instead send the user to a redirect-laced malicious URL that fires off a variety of scripts.
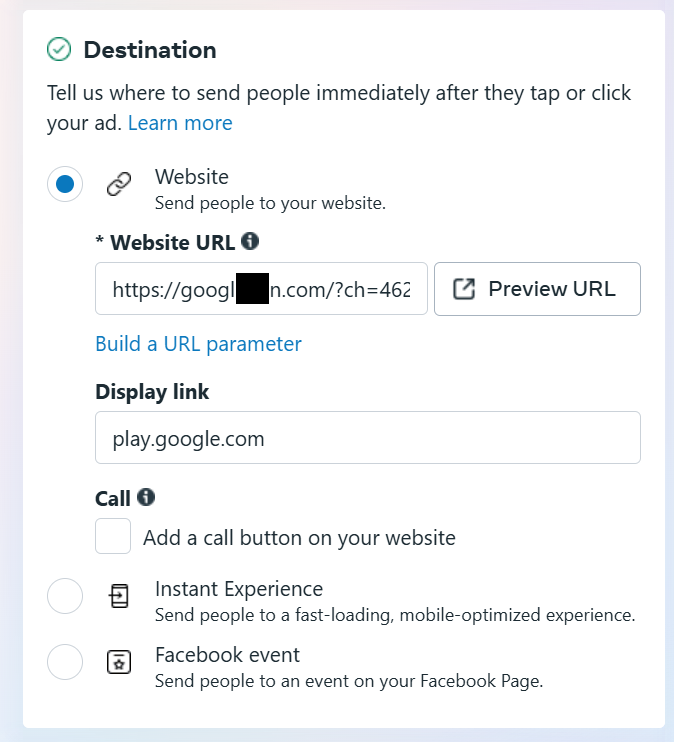
I struggle to come up with many sensible reasons why Facebook would deliberately work in the option to present one URL in the depicted ad to the end user, while allowing it to actually redirect to any other domain they want. This seems ripe for deceptive intent. To impede this even further, a user cannot even hover over or copy the hyperlink to determine the true destination because they all redirect through a cryptic Facebook URL to start.
Ad Reach and Impact
All told, 31 unauthorized campaigns ran while my account was disabled. They were all designed to be "ongoing" and effectively a bottomless financial limit. Some variants of ads were attempted at the end, including the "promotion" of some other profile or page. That final one was thwarted before it could grow legs, at least from my account.

The cumulative total of these ads had a reach of 459,906 users, a total impression count of 624,148 and cost $10,160.07. This unauthorized exploitation of the Ads Manager has led to my personal ad account being currently disabled and inadmissible to create new ads, which for the moment I'm fine with until the dust settles and I'll attempt another appeal in light of the proven session hijacking that led to it.
Residually Damaging Effects
When a Facebook account gets disabled or suspended, there are far more potential implications to the victim than just the loss of contacts, memories and years of content. Facebook has long been one of the mainstay third party authenticators for logging into other services and websites. For many users, it is more convenient to use an existing Facebook account than the tedium of registering all new for services.
Among dozens of others, I have used my Facebook account to register or otherwise link to:
- Oculus
- Kickstarter
- Epic Games
- McDonald's
- TikTok
- Zillow
- Patreon
- Wish
- Scribd
- Restaurant.com
- Unsplash
- Mighty Networks
- Spotify
- Nextdoor
- DailyMotion
Many of these services may now be inaccessible or require additional complex hurdles to convert from the original Facebook sign-in to an original login.
Especially damaging is the inability to use my various Quest and Oculus Rift VR headsets. As a day-one user of the original Oculus Quest DK1 through present, with many games and packs purchased through the Oculus store, this is an inexcusable loss in use over a completely disassociated Instagram exploit.
Possible Avenues to Restore Account
If your original account has been disabled due to the fake linked Instagram account, right out of the gate you are in for a perplexing challenge to get it restored. This is because Meta/Facebook advise you that the only way to appeal is not through your genuine Facebook or Instagram account, but rather through the malicious Instagram account that they deleted.

Got it! All I have to do is magically gain access to the clearly bot-generated, rightfully deleted Instagram account named "p9npvdn" that was maliciously associated with my account and only for two minutes at that before it was wiped out, to appeal the disabling of my 17-year-old Facebook presence...Wait. What?
To add salt to those wounds, they also start a countdown of 30-180 days before they assure you the account will be permenantly and forever erased and all the years of memories, contacts and media. Many submit appeals and hear nothing back for an indefinite amount of time. Some have sent physical letters to various Meta addresses to similar non-response.
There have been several local media stories covering this fiasco by others who have had their accounts disabled in this same manner, dating back to at least 2022.
- October 23, 2024: Knoxville Woman Wants Answers after Facebook Account Disabled
- November 8, 2022: Facebook and Instagram Unresponsive to User after Accounts are Disabled
Meta Verified
The most common path toward at least reaching someone in Meta's support system is to become meta verified. This is a paid monthly service that offers entry level support options including via chat or email. If you have an Instagram account that was previously linked to your Facebook account or at least has some connecting data with your suspended Facebook account, you can consider becoming Meta Verified on Instagram by following the steps within the app.
Instagram Profile > Settings and Activity > Meta Verified
Depending on the status and longevity of the account you are applying for, as well as your location and other unspecified criteria, you may get approved within minutes or end up on a waiting list that might take months to reflect any change. Once approved, you can use the Instagram app to "Get Support" as one of the paid perks. You will have the option of chatting (0-20 minute wait time) or via email (1-14 day wait time).
My first effort was to send a detailed email describing the hack and impossibilities of appeal using the ordinary means, since it related to an Instagram account that I had no involvement with. The three essential details the support team requests as part of potentially restoring an account are:
- The username or URL of your Facebook account. This is usually a unique username you specified when defining a custom URL, which Facebook started encouraging many years ago. This can be found in your downloaded profile content under "Profile Information" as described earlier, or retrievable from your browser history or by asking a friend who corresponded with you to click into your (ghost) profile to get the URL.
- The date that you first noticed your account was hacked or disabled. This will be obvious to any frequent user of Facebook, but you can also find the specific time that the intruder overtook the session and ultimately when the account was disabled by reviewing the "Account Status Changes" in the downloaded content.
- An alternate, unassociated email account. If your account is successfully restored, reset instructions and correspondence will be sent to this new detached email account to ensure the attackers do not regain access to any of your credentials.
Whether you use chat or email, be prepared for days and weeks of delays between outcomes. Also brace yourself for those outcomes to be similar to my own after the first week of email attempts. My first chain of email correspondence ended with boilerplate: "...we are unable to take any further action from our end, please review facebook.com/hacked" and was of no help at all since it isn't just a compromised or hacked account, but a suspended/disabled one as well. No amount of reporting your account as hacked or getting it ID verified will overcome that obstacle.
I subsequently reached out via chat directly and this time with the cause being "Account Hacked" instead of "Account Disabled" and am nearly a week into waiting for any response on that one, too. I will update this post with any further developments from my perspective. (01/03/2024 Update: See "Facebook Account Restored" section below.)
Those who manage to have success through the Meta Verified path of support, often only see such success after repeat attempts in hopes that one lands on the desk of somebody with the toolset and knowledge to proceed beyond just reciting a script. As an IT professional, this lack of support and inability for them to easily identify obvious hacked account situations like this and revert back to the pre-compromised state can be exhausting.
Meta for Business or Oculus Support
If you have an existing business account and have previously served ads on the platform, you may have success reaching someone in that realm to assist. However, unless you have prior contacts with them through phone or email, the ordinary Meta for Business support ticket system requires that you already be logged in through your Facebook account.
The other avenue that proved successful with many years ago was through the Oculus website. My impression is that this sort of support for disabled Facebook accounts as part of Oculus sign-up has weaned since 2021, but it is certainly worth a shot especially considering many Oculus accounts may be tied to hundreds or thousands of dollars of now inaccessible software until the account gets reinstated.
Legal Action and Small Claims
An increasing number of disabled account holders have began reaching out to their Attorneys General and small claims litigation.
- March 6, 2024: 41 State AGs Tell Meta to Fix Their Customer Support for Hacking Victims
- May 4, 2024: Why Attorneys General are Fed Up with Facebook
- June 20, 2024: How Small Claims Court Became Meta's Customer Service Hotline
This is a complex endeavor but one that at least from numerous documented instances online can hold greater weight in influencing the decision for an actual human at Facebook to look into it.
The crippling downside to any of these means to restore an account is that they can consume months, even years of time. All while Facebook's promoted "180 day" deadline to appeal anything looms. I have read heartbreaking accounts by users who had their entire support system for rare medical conditions or deceased loved ones ripped from them and then watched the 180 day appeal window diminish to nothing with no action to resolve it by Facebook.
Second Level "Recovery" Scams: Don't Fall For It
As soon as anyone vents about Facebook online through other social media outlets, they will be bombarded by replies and private messages with people who insist they "know a guy" who can get these accounts recovered.
This is an added layer of scam and exploitation of the most desperate and vulnerable. There is nobody outside of Meta that can help you restore an account. They have no added toolsets or means to get this done. You will pay a non-refundable "service fee" ranging from $30 to $250+ to a random stranger online who will ultimately fail to restore anything.
Worse, many of these opportunists will ask you for sensitive, confidential information including your account credentials, answers to security questions and a host of other personally identifiable details that will allow them to gain access to even more of your accounts for added damage.
To further the anguish, if you get scammed by the recovery scams, you may even find a third layer to these operations in which another "entity" contacts you to claim they can get your money back, for another service fee or more data turnover. 😜
Facebook Account Restored
After approximately two weeks, I finally reached a level of support and offered enough empirical evidence to establish the nature of the hack, which I had no control over it. This included supplying numerous screenshots and concise narratives similar to above that detailed the entire scenario and pinpointed the precise timeline of events. After several circular conversations with a Meta Pro support member, I advised that if these repeat questions and answers were to continue then it would be more timely to refer me to their supervisor. I again emphasized how the loss of my account was causing great harm to my personal and professional self, with nearly 18 years of contacts, groups, pages and content at risk.

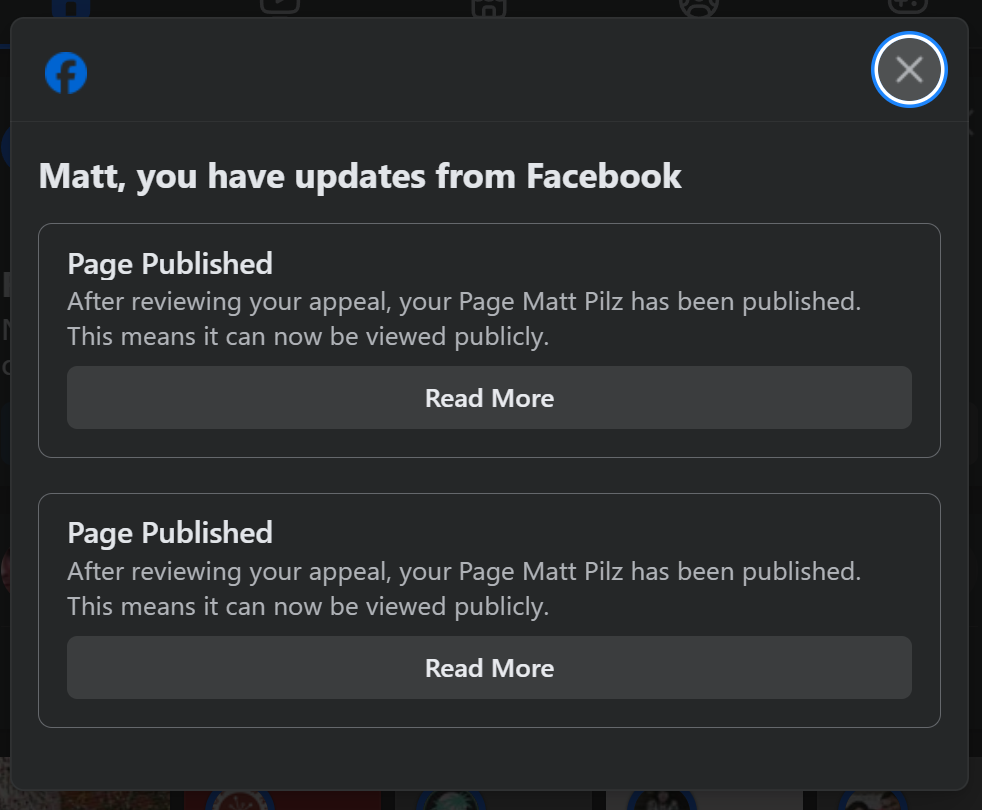

As part of the recovery and reset, a new temporary login code was sent to the fresh email address I provided. From that I was able to login and walk through a wizard of steps to help remove some of the changes made to my account following the hack. There were some rogue entries including following an unknown account, and the above mentioned "page" that was serving up the ads.

Facebook's final message explained: "We found that our technology made a mistake adding restrictions to your account. Thank you for taking the time to request a review and helping us improve our systems. Our priority is keeping the community safe and respectful, so sometimes we have to take precautions."

Unfortunately my Meta account that was tied to my longtime Oculus/Quest profile and apps is disabled due to the same rogue Instagram issue. This has made it impossible to download the screenshots and videos I had recorded directly to my Quest or to obtain any of my previously purchased titles. While I could start the recovery process for that account, this singular effort has made me less than ambitious. In the interim I have linked a Meta account tied to my clean email account and a factory reset of the Quest should revive it to an extent.
At some point in the future if I would like to publish genuine ads on the Meta platform, I will also need to appeal that disabled status. But for now I am just content knowing my Facebook and all the memories it contained is back to normal.
(Update 01/09/2025: My original Meta account has now been restored. The original offending fake Instagram account was still listed under Accounts Manager for it, as a disabled account.)
Securing your Accounts
The root of this Facebook "hack" doesn't necessarily come from poor account maintenance by the end users. Since it is a cookie hijack type exploit, even users with sophisticated passwords and 2FA are at risk. From Facebook's own perspective, they should absolutely 100% be retriggering multiple layers of 2FA requests (both email and text confirmation, at a minimum) before allowing any other account on any of their platforms to be linked to another. The one-click convenience of being "always logged in" or to instantly share cross-platform is not worth the potential of being "always locked out" when an exploit like this occurs.
That said, some final words of wisdom before I conclude this article and await my own next steps at challenging the disabling of my account:
- Minimize your use of browser extensions. As evidenced as the likely culprit in this attack that impacted potentially millions of users, a common weak point that can enable cookie theft comes from browser extensions. Even ones that make their way to official outlets like the Chrome Web Store or Firefox Browser Add-Ons can hold some stealth vulnerabilities or deliberate malware. I'd personally recommend deleting every extension and then starting over, with perhaps the most basic (e.g., Ublock Origin). Otherwise it tends to gradually grow much like an app screen on a phone, in which you end up with many extensions that aren't actively useful to you that should be uninstalled.
- Use privacy and cookie-conscious browsers. Most browsers are becoming more privacy-centric with the disabling and anonymizing of third party cookies. But for maximum security and built-in adware blockers for mobile and desktop, there is Brave
- Clear your own browser cookies regularly. It is undeniably inconvenient to clear cookies in a browser. Unlike deleting cache, deleting cookies will log you out of any sites and have the potential of erasing other session-specific data like shopping carts. But making a habit of this will ensure there are no stale sessions lingering around for too long.
- Keep your virus protection up-to-date and don't click any unknown links or downloaded documents. Many cookie stealing exploits rely on the host opening a script or stealth executable that can readily grab browser cookies and send them to an attacker. Exercise caution whenever dealing with newly downloaded programs. Scan them at VirusTotal.com, too. Windows Defender works well, but make sure you have could detection enabled to help with 0-day exploits.
- Learn to Love 2FA. Set up multiple authenticators, text/SMS alternates, and safely store backup codes that are provided for future account recovery purposes. Add all levels of extra security the services provide. Enable as many notifications about login attempts as possible.
- Delink your Accounts? While there are obvious conveniences of linking your Facebook, Instagram and Meta accounts together, the lack of extra security precautions by Meta in doing so and gung-ho disabling of all associated accounts, by proxy, in the event a violation is found makes this not so desirable. Had each one of my accounts been an isolated instance, the parasitic Instagram account would had never found its way over to my Facebook and Meta profiles. In this way, there is a strong argument to be made for delinking any of your Meta accounts so that one will not affect the other in case something goes haywire.
Closing Thoughts
What should had been a time of relaxation and celebration instead devolved into depressing, all-consuming thoughts of loss due to this Facebook-Instagram exploit that I, nor any others, had control over. While we are just a speck in the field of billions, within that dot on Facebook were nearly two decades of memories, contacts, support groups and cherished content shared among family and friends. To have all of this ripped out without notice or warning, due to some attacker across the world and two minutes of carnage, is soul-crushing.
While I had reasonably timely success at getting my account restored, I know many others have been attempting the same for months if not years. It would be in Meta's best interest to refine security policies and figure a way to expedite easily provable hacks of this nature that are out of the end user's control or knowledge.
If you were affected by the latest batch of Facebook disabled accounts, or any others, feel free to chime in your experience below.



