Over the years I have established a fair number of email accounts, the oldest of which have long been overtaken by spam to the point that checking them is a futile endeavor. Rather than just shift-deleting all of the messages, however, I thought it might prove fun to technically analyze some at random.
RE: Notification – Registration Registration
Today’s scam email is allegedly1 brought to you by “Customer Contact Manager – PO Box 4668 New York, NY 10163.”
The full email I received is presented below:
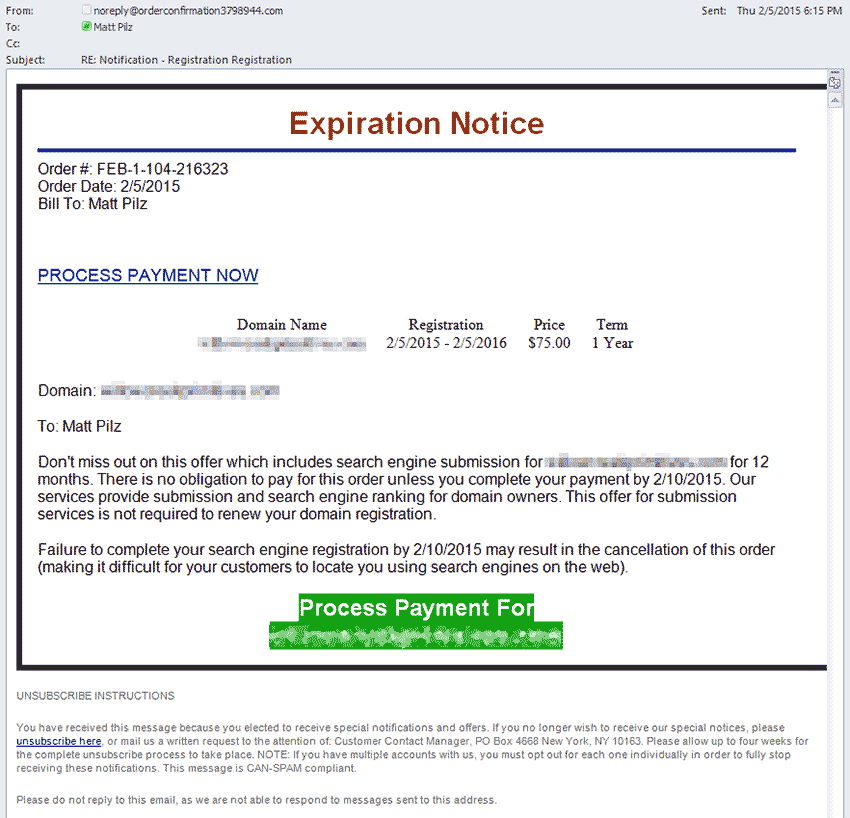
The email is arguably a step above many common scam messages in that it uses some personally identifying details to lure in the victim. The details are scraped from public WHOIS information, albeit outdated, and the email is formatted structurally to resemble a run-of-the-mill expiring domain notice. It lists a legitimate domain name that I own, along with the price to renew it for another year.
Reading the blurb of text below the PROCESS PAYMENT NOW link raises an eyebrow while subtly conceding that the alleged payment is not really for any sort of domain renewal. Instead, the spam message promises that by processing the payment they will perform “search engine submission and search engine ranking 12 months.” But, I must act fast because if I don’t complete my “search engine registration” by submitting payment information within five days the order may be canceled, thus “making it difficult for your customers to locate you using search engines on the web.” How unfortunate.
Of course, there are no actual costs to submitting domains to search engines. In fact, shortly after I created this blog I observed it had already been indexed on Google with no intervention required. Modern search engine spiders are fairly proficient at picking up new content on a regular basis. For the ambitious souls out there, search engines also provide simple forms to manually submit URLs for future crawls (Google | Bing | Yahoo). But let’s take the spam for a test-drive anyway.
Technical Summary
The sender’s return email address and domain seem totally legit: orderconfirmation3798944.com. The landing page Store itself is a simple login portal powered by PHP. To my surprise, the page does use sprinklings of modern HTML5 and CSS3 syntax, including new input types like ’email’ and some rounded borders. Many simple scam pages I come across like this still use archaic design methodologies, some even dating back to FrontPage 2000. Anyway, there is not much to see here. The form posts back to itself and returns an ‘invalid user’ error. Apart from the built-in email field checking of HTML5 no other validation is conducted and you can even leave the fields blank if you wish. Analyzing the single CSS file on the server suggests that this is all there is to see, with no alternative formatting under any circumstance.

The actual “Invoice” page linked from the email is marginally more interesting. It again reiterates the domain name and billing information as retrieved at some point in time from WHOIS data. The page developer made a slight blunder in the “Bill To:” DIV section by adding a class=”editable” tag to it. I presume the intent was to instead add the contenteditable=”true” attribute to the DIV which would then allow the one being scammed to edit the billing – address to their current location or that which matches their credit card. As it stands, there is no way to edit the billing address on the page.
You are given the option of renewing for 1 year ($75) or 2 years ($135; a $15 savings!) and then asked to enter your complete credit card information including CVV number. My favorite part is that the heading reads “Secure Online Payment (128 Bit Secure)” and displays a couple SSL security badges merged into one image. The page is of course delivered via fully unencrypted HTTP and actual SSL certificates for it are delivered purely by imagination.
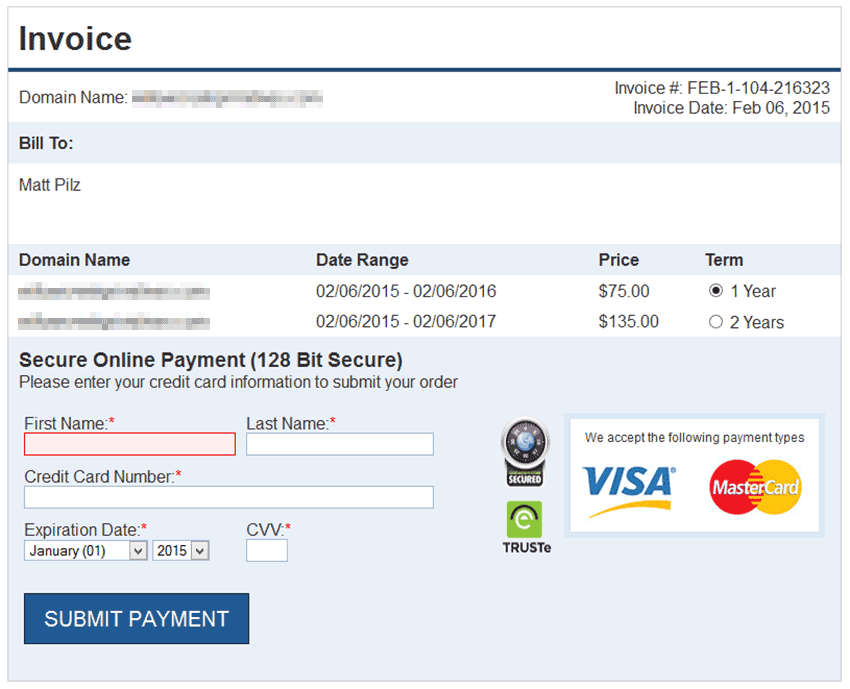
The ‘invoice’ page that users are directed to upon clicking the link in the email.
This page includes a single JavaScript file that performs some client-side validation of the various fields using jQuery 1.11. For the credit card information, the standard is used in conjunction with regular expressions to check the general validity of each field (the max length of the CVV field is adjusted dynamically based on the credit card number being detected as Visa or MC).
Now the dangerous part. With structurally valid credit card information entered and submitted, the data is serialized into a plaintext string and then sent in a postback loop via an unencrypted POST method. On the server-end, this data gets passed to a third party payment processing vendor for final validation and currency withdrawal. The processor returns a response which is sent back to the scam page as a JSON object, with an indication of whether the credit card was approved or why it was denied.
Based on analysis of the response data, it appears the data is ultimately submitted through a BeanStream-powered payment gateway for processing, a popular system with API access through PHP and not part of the scheme itself. If the payment is unsuccessful for any reason (i.e., invalid card), the resultant scam page will append HTML to a DIV stating: “Transaction declined. Please check your card and try again.” If successful, a redirect will take the user to a ‘Success’ page of sorts, now $75-$135 poorer (not to mention the likelihood of your plainly transmitted credit card details being stored in a remote file for future access).
The base domain is hosted through DNSPod, a China-based service rampant with spam (although DNSPod vowed to crack down on spammers years ago). The same IP hosts countless other domains registered in January with the same pattern: orderconfirmation#######.com. The content itself is mirrored at each domain and is hosted on an Apache 2.2.15 server (CentOS) at a separate IP.
1 I use the term allegedly when describing the location here since spammers often include fabricated addresses as part of their content. If you Google the referenced address, you will find many questionable references to it.



